Funded by NSF Cyber Trust CNS-0627318: “Collaborative Research: CT-ISG: Modeling and Measuring Botnets” (in collaboration with Dr. Wenke Lee from Georgia Tech)
Project Description
A botnet is a network of compromised computers, or bots, commandeered by an adversarial botmaster. Botnets are responsible for many attacks, including spam, phishing, key logging, and denial of service. This project aims to develop techniques to model and measure botnet propagation and on-line population dynamics. Knowing the trend, size, and locations of the population of a botnet can help estimate the potential threat of a botnet, and select and prioritize the appropriate response actions.
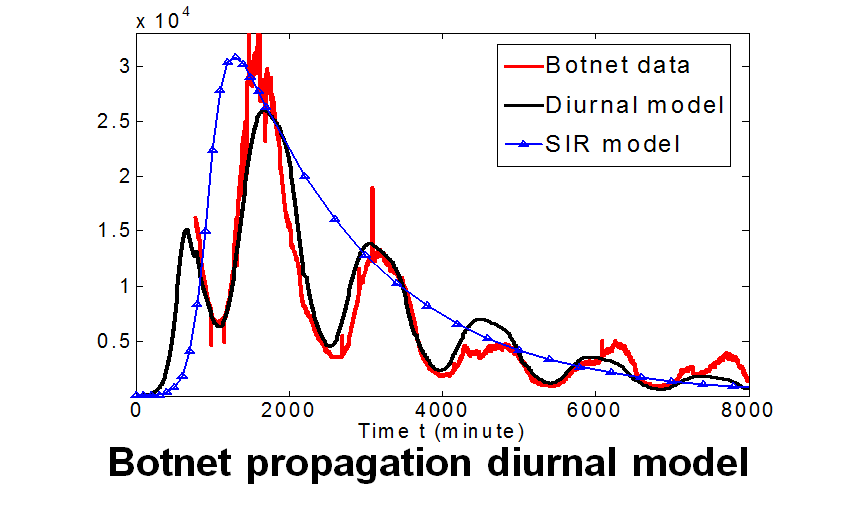
Although Internet worms are often used to create botnets, there is fundamental difference between them. Worms are typically designed to infect as many machines as possible, and are in general “noisy” and easily detected (and thus removed); whereas botnets are designed to evade detection, and control and make use of the compromised machines for as long as possible. The existing worm models focus on the initial/short propagation phase of a worm. But a good botnet model needs to track the dynamics of botnet online population in the long run.
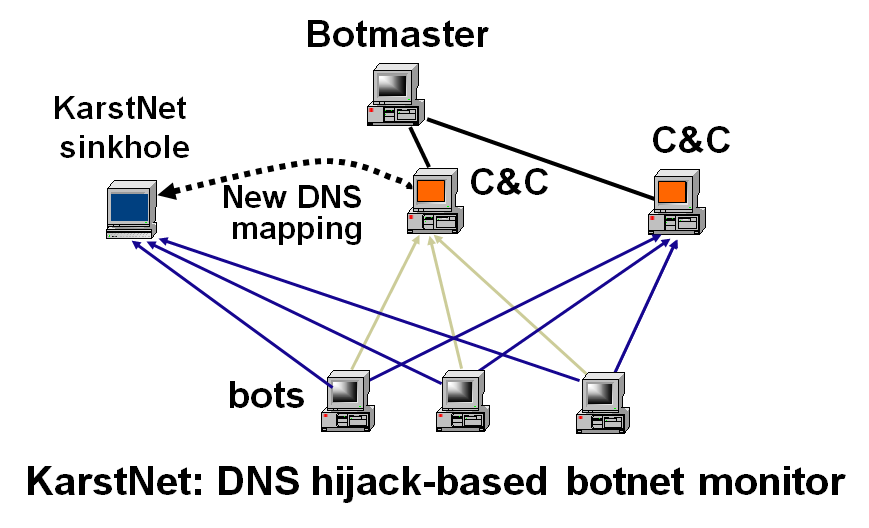
This project has three main tasks. The first is to develop diurnal models to track the grow-and-decline trend of botnet on-line population using factors such as time zones and distribution of vulnerable systems. The second is to develop sampling and measurement approaches including capture-and-recapture and DNS cache snooping to estimate the total population of a botnet. The third is to develop measures for threat assessment, e.g., its aggregated bandwidth and resilience to response, based on the system, location and topology information of the bots.
Publications:
- David Dagon, Cliff C. Zou, and Wenke Lee. “Modeling Botnet Propagation Using Time Zones,” in 13th Annual Network and Distributed System Security Symposium (NDSS), p.235-249, Feb. 2-4, San Diego, 2006 (Acceptance ratio: 17/127=13.4%).
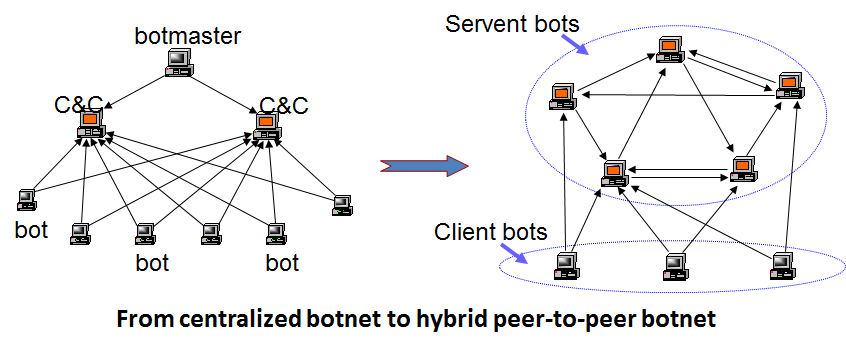
- Ping Wang, Sherri Sparks, Cliff C. Zou. “An Advanced Hybrid Peer-to-Peer Botnet”, IEEE Transactions on Dependable and Secure Computing, 7(2), 113-127, April-June,2010.
- Ping Wang, Lei Wu, Ryan Cunningham, Cliff C. Zou. “Honeypot Detection in Advanced Botnet Attacks”, International Journal of Information and Computer Security (IJICS), 4(1), 30-51, 2010.
- Ping Wang, Lei Wu, Baber Aslam, Cliff C. Zou. “A Systematic Study on Peer-to-Peer Botnets”, International Conference on Computer Communications and Networks (ICCCN), San Francisco,Aug. 2-6, 2009.(Acceptance ratio: 114/387 = 29.5%)
- Cliff Zou, Don Towsley, Weibo Gong. “Modeling and Simulation Study of the Propagation and Defense of Internet Email Worm,” IEEE Transactions on Dependable and Secure Computing, v.4, 2007, p. 105.
- Ping Wang, Baber Aslam, Cliff C. Zou, “Peer-to-Peer Botnets: The Next Generation of Botnet Attacks”, in Stavroulakis, Peter; Stamp, Mark (Eds): Handbook of Information and Communication Security, Chapter 18, Springer Press, 2010, pp. 335-350.
